Altera Forums Read Fail Read Again Successful
How to hack Wi-Fi in Windows
There are not any costless Windows-based tools for wireless audit, are in that location?
There are!
Router Scan – free Windows programme with GUI to browse networks and hack routers – got new amazing features. Now you tin can perform Wi-Fi security inspect from Windows.
New Router Scan by Stas'M features
In Router Browse since v2.60, wireless audit capabilities have been implemented, they include beast-force attack against WPA/WPA2 key of a network, obtaining a password using the WPS PIN, and Pixie Dust attack.
Download the latest Router Browse
Go to the program folio and click the Mirror download push button:
Unzip the archive and run the RouterScan.exe file.
What exercise I need to use the wireless audit capabilities of Router Browse?
Programs
If you lot run across error messages when trying to use the wireless audit functions:
[-] Raw packet capture not bachelor. [*] Delight install WinPcap and try again.
So you need to install WinPcap, a link to download (choose the version for Windows): https://www.winpcap.org/install/default.htm
So you need to install Npcap, link to the official page where y'all will find the installer: https://nmap.org/npcap/. When installing Npcap, be sure to check the "Install Npcap in WinPcap API-uniform manner" checkbox!

Hardware
To creature-force WPA-PSK key (in other words, the countersign from the Wi-Fi network), any Wi-Fi carte du jour should approach, since the Router Scan just try to connect using dissimilar passwords in ordinary mode. If you have several wireless dongles you should give preference to ane that sees more networks and keeps the bespeak better.
In the attacks on the WPS PIN when using Alfa AWUS036NHA I received an fault message:
[-] Failed to beginning raw package capture. [-] Try updating your Wi-Fi driver and/or installing Npcap in WinPcap-uniform mode.
Since my second Alfa AWUS052NH adapter works with Router Scan fine, it is more long-range, and I mostly utilise information technology, including Linux, I did non try to cope my issues with AWUS036NHA. Possibly the problem could be solved in the recommended way. By the way, write in the comments, what wireless adapters work with Router Scan well, and with what problems you occurred.
Since WinPcap too contains the driver, I would non be surprised if even wireless cards that are unsuitable for use in Wi-Fi auditing in Linux due to commuter limitations are suitable for WPS PIN attacks in Windows. I cannot verify this, considering at mitt there is no 'usual' Wi-Fi adapter.
Built-in Wi-Fi adatper Intel Corporation Centrino Avant-garde-Due north 6235 (rev 24) (in Linux it supports monitor mode and injection) also works well with Router Scan.
Configuring Router Scan
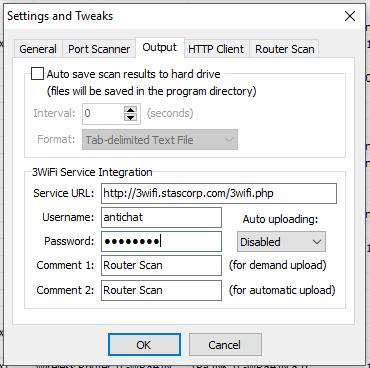
For some of our attacks, we demand information from 3WiFi. Guest access is enough for our needs. Get to the Router Browse settings and enter "antichat" as Username and Password:
Overview of wireless networks in Router Scan
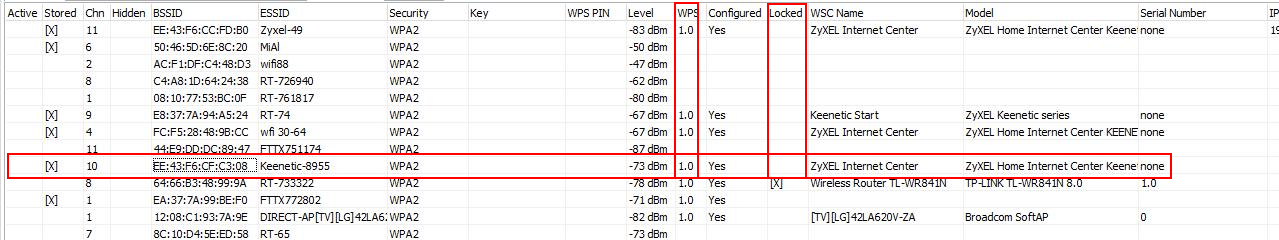
In Router Scan, since version v2.60, the Wireless Networks tab has appeared:
In the Interface field, select the Wi-Fi adaper that y'all want to use for auditing Wi-Fi networks. If you bank check Enable discovery, data will be collected most available access points within reach. To prevent access points from disappearing from the list, tick the Cumulative mode:
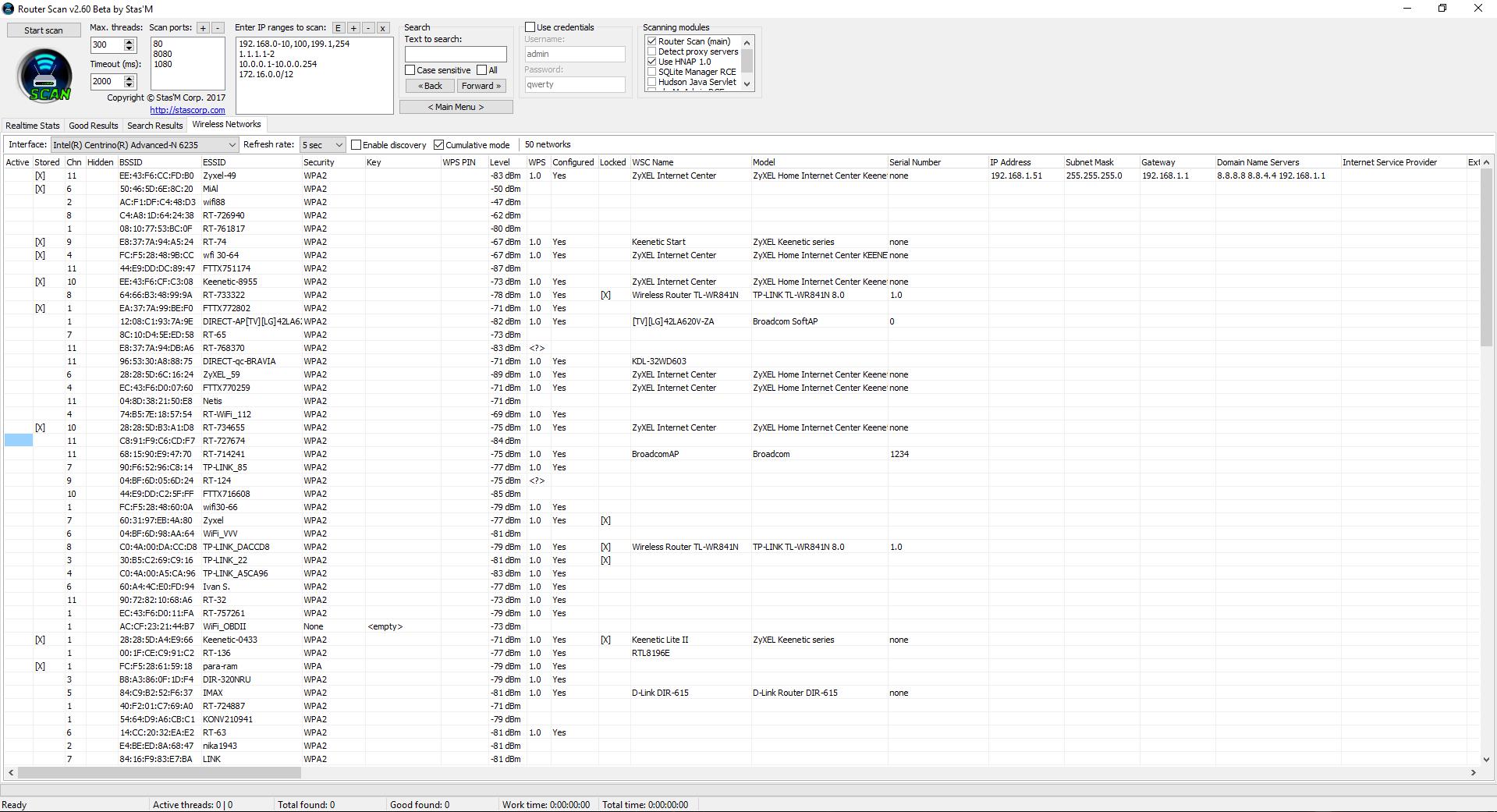
The Agile column marks (seemingly) the networks to which you lot are currently connected.
Please note that we accept admission to avant-garde information about access points. Y'all tin can see the exact model (WSC Proper name and Model fields) for the AP with WPS.
Getting a WPA password based on the predicted WPS Pin in Router Scan
In one of my articles entitled 'Effective WPS PINs set on based on known PIN and Pivot generation algorithms', I talked virtually this method of fast Wi-Fi hacking, when WPS PIN is calculated on the basis of algorithms, or taken from the database. If the PIN is guessed, then the password from the Wi-Fi network is revealed.
Approximately the aforementioned attack is implemented in Router Scan. The program contains the WPS PIN Companion tool. This tool 'guesses' the WPS Pin of the wireless network. The Pivot is calculated by certain algorithms, based on the MAC-address and series number of the router (but for some generation algorithms). In the new version WPS Pin Companion received new algorithms and other improvements, but the master thing is its combination with another tool, which in the context menu (chosen past the right mouse push button) is named Obtain key with WPS …:
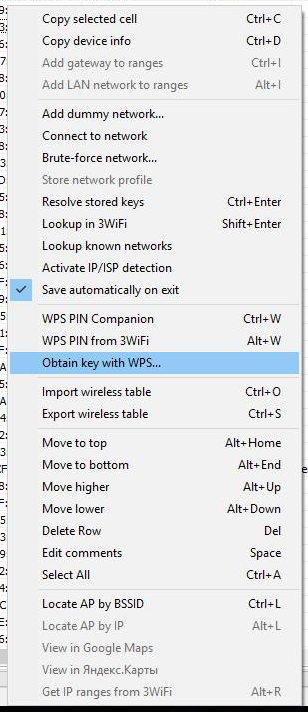
Since only access points with WPS are suitable for hacking, it is necessary to select those with a version number in the WPS column, and nothing is written in the Locked column (i.e. WPS for this AP should not exist blocked), an instance of an appropriate point access:
Click on the selected AP with the right mouse push, select Obtain key with WPS …:

If you already have a WPS PIN (or several pins), enter them in the PINs field. If you do non accept a pin, then close this window.
2 options are also bachelor in the context carte du jour:
- WPS PIN Companion
- WPS Pin from 3WiFi
The first calculates the PIN for a given access point by algorithms:
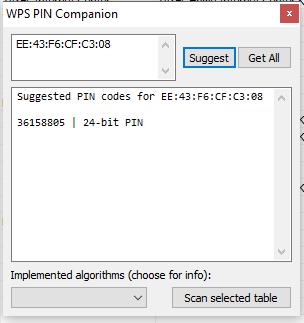
As you tin can see, the guessed pin is 36158805.
When you click on WPS Pin from 3WiFi, the following window is displayed to u.s.:
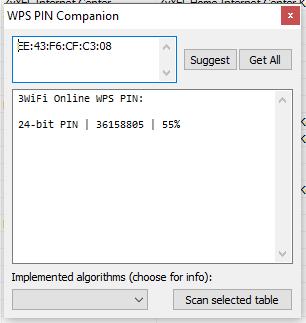
In it again 36158805 and, evidently, the percentages of coincidence.
Let's return to the pick Obtain key with WPS …:
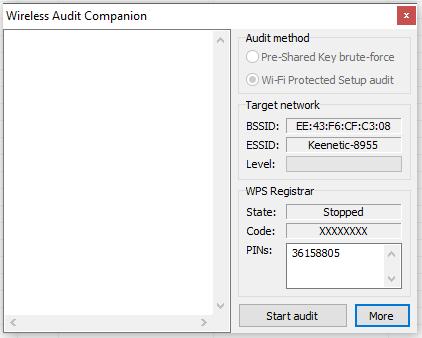
Our pin is entered automatically, press Start audit.
As you tin can meet, the countersign is successfully cracked:
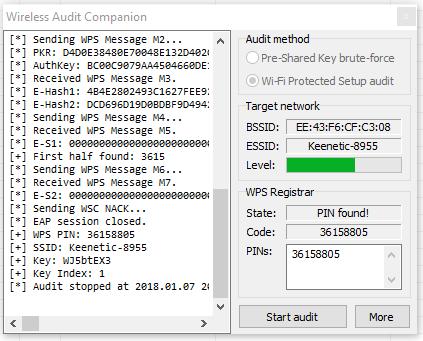
This is indicated past the lines:
[+] WPS Pivot: 36158805 [+] SSID: Keenetic-8955 [+] Central: WJ5btEX3
The password from Wi-Fi is WJ5btEX3.
Brute-force password from whatsoever Wi-Fi network with Router Scan
The previous method is fast, but works but for networks with unlocked WPS.
For all other access points, a more than universal but slower method is bachelor. Its essence lies in the fact that Router Scan tries to connect to the Wi-Fi network with a password that it takes from the dictionary. If the connexion was successful, so the password is guessed, if the connection did fail, then the program proceeds to the next password and tries information technology, etc. Side by side, until the password is croaky or the dictionary is completed. Every attempt takes a few seconds - it's slow.
To start the attack, right-click on the access point of interest to you and select Brute-force network …:

The attack must begin with the selection of the dictionary file. To exercise this, opposite the Dict field, click (click to load) and select the dictionary file. With the plan comes a small dictionary (file wlanpass.txt) for 90 words. You tin can utilize it.
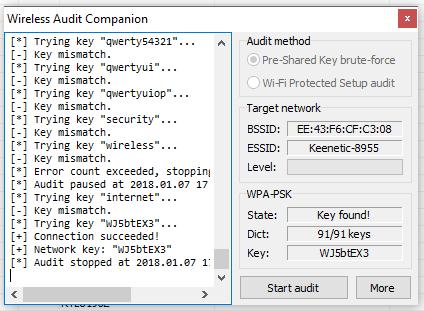
Successful countersign great:
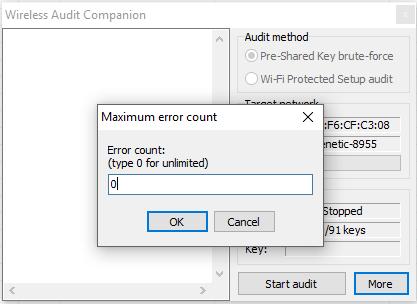
Past the mode, and then that attempts exercise not cease, click on More, then Maximum fault counts and enter 0 for unlimited attempts:
View passwords from Wi-Fi to which the computer was previously continued
Router Scan allows you to become the passwords from the networks you lot was previously continued to. To do this, select the Resolve stored keys selection from the context menu:
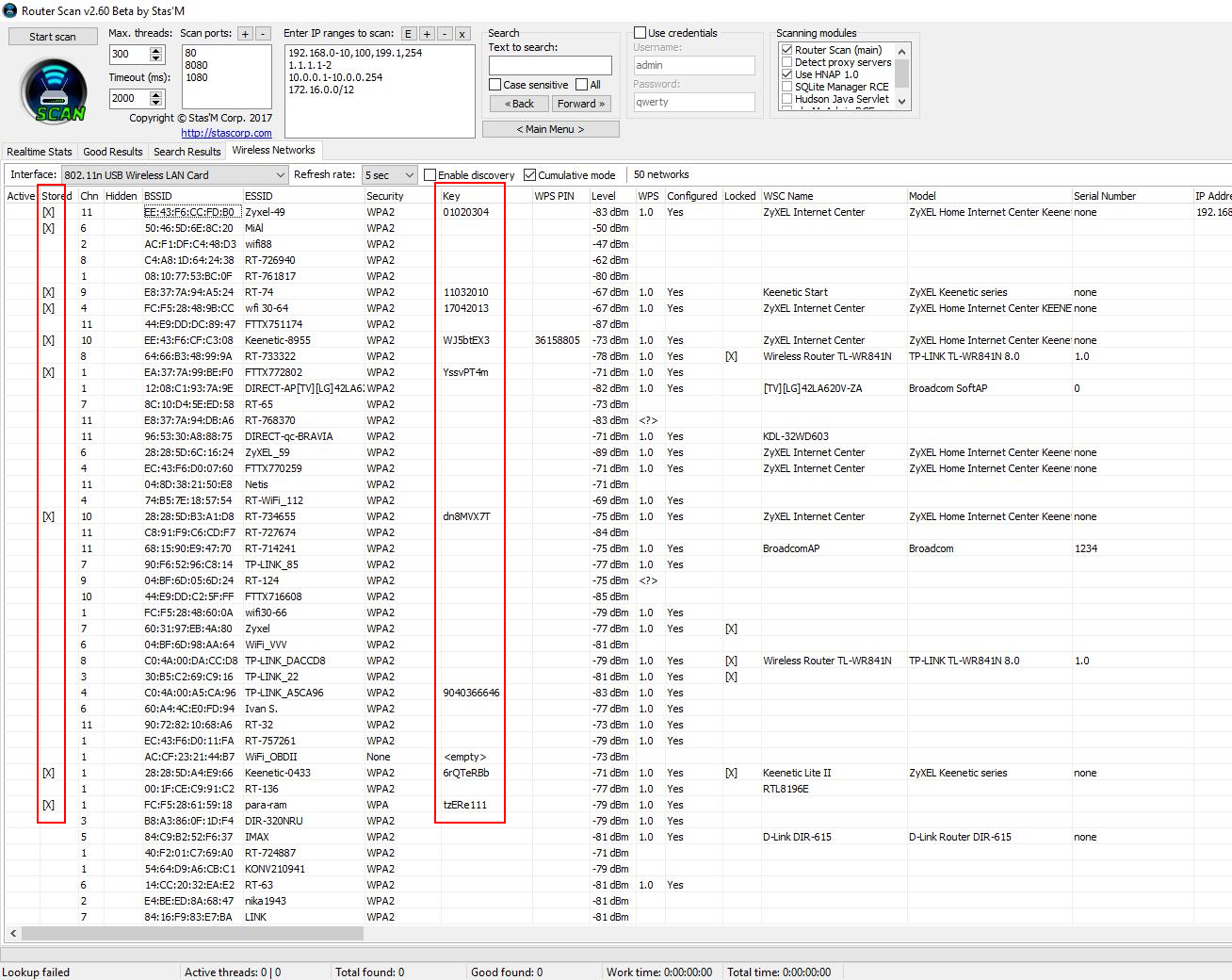
How to determine the location of Wi-Fi
To do this, in the Router Scan select the Locate AP by BSSID choice, the following window will appear:
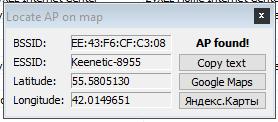
For example, click on Google Maps:
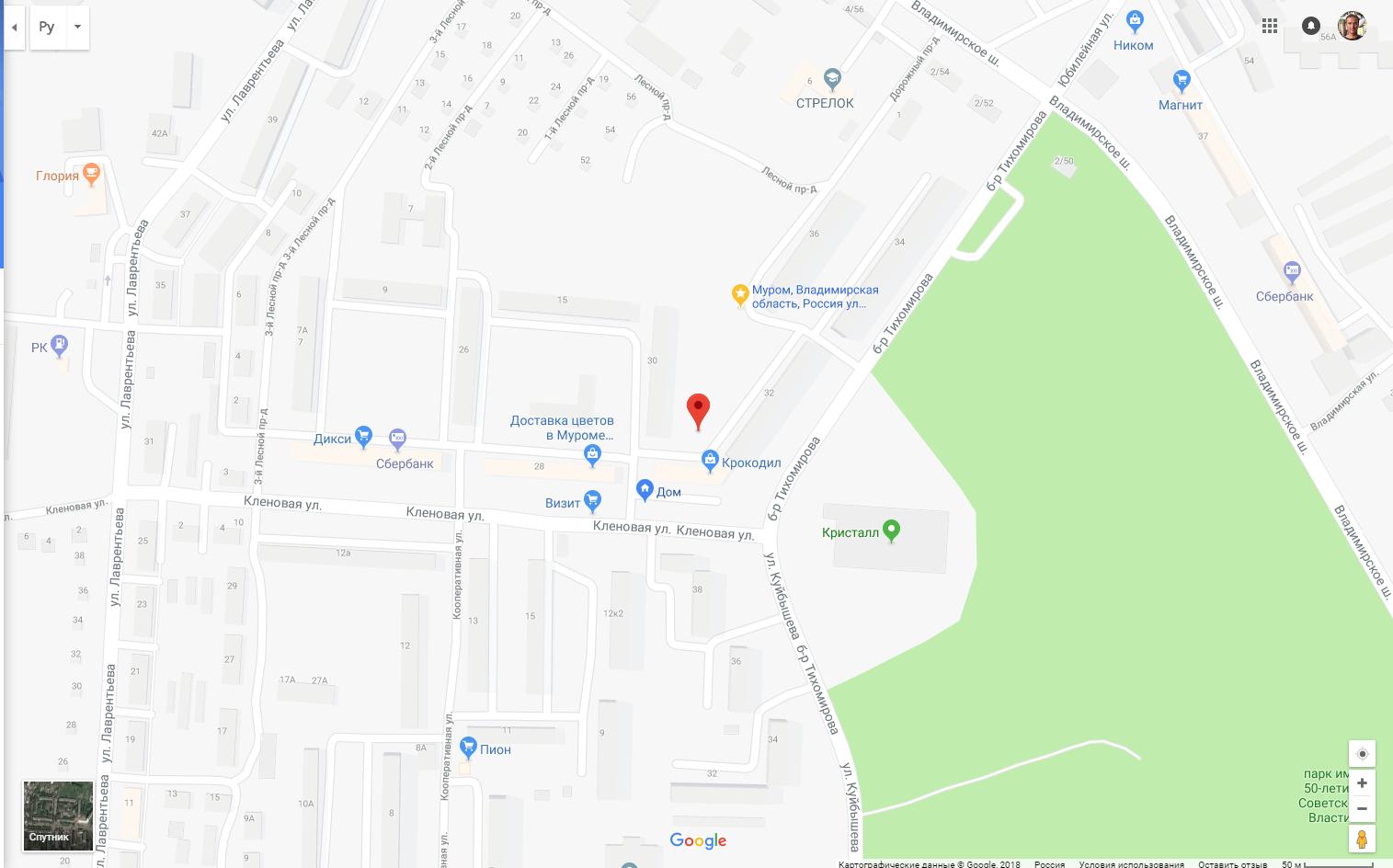
Trouble solving
i. Endless fault "Association failed"
Sometimes when I attacked Wi-Fi, there were endless letters:
[*] Associating with AP... [-] Association failed. [*] Associating with AP... [-] Association failed.
If you lot stop and restart the set on, this mistake usually disappears.
The Wireless Networks tab does not work on Linux.
2. The Wireless Networks tab does non work on Linux
The Wireless Networks tab does not and will never piece of work on Linux, equally this functionality in Router Scan requires WinPcap or Npcap, which are not available on Linux.
iii. Npcap is installed, simply withal the error "Please install WinPcap and try once again"
If yous've already installed Npcap or installed Wireshark, simply still get the fault:
[-] Raw parcel capture not available. [*] Please install WinPcap and endeavour again.
The reason may be that you lot forgot to enable the "Install Npcap in WinPcap API-compatible manner" checkbox. Restart the Npcap installer and enable this option.
4. Wireless attacks do not piece of work in Router Scan
If your Router Scan wireless attacks stopped working, there is now a fix.
Router Scan relies heavily on WinPcap/Npcap for wireless attacks. In the Npcap changelog (https://github.com/nmap/npcap/blob/chief/CHANGELOG.md) we can run into the following:
Npcap one.xxx [2021-04-09]
Restore raw WiFi frame capture back up, which had been broken in a few ways since Npcap 0.9983. Additional improvements enable PacketSetMonitorMode() for not-admin-privileged processes, allowing Wireshark to correctly enable monitor style via checkbox without requiring WlanHelper.exe.
In short, the functionality associated with wireless attacks has long been broken. Now they fixed it – I checked, the attack on WPS was successful.
Then just update Npcap to the latest version. Alternatively, install the latest version of Wireshark – Npcap comes with it.
Decision
Router Browse Stas'Grand is a unique and like shooting fish in a barrel to employ plan, it has no analogues for either Windows or Linux. New Router Browse features in many means are as well unique for Windows. Notwithstanding, Linux OS can offer additional tools for attacks on the Wi-Fi network.
Source: https://miloserdov.org/?p=712
0 Response to "Altera Forums Read Fail Read Again Successful"
Post a Comment